プライベート認証局を利用してSPICEサーバのTLS暗号化設定方法について日本語で説明しているサイトが少ないのでまとめておく。ついでに virt-manager のTLS接続設定も行う。
目次
- 環境
- うまく行かなかった…
- プライベート認証局の構築とサーバ証明書の発行
- SPICEサーバのTLS暗号化設定
- virt-manager のTLS接続設定
- おまけ(クライアント証明書を失効させてみる)
1.環境
CentOS:7.6.1810(Kernel:3.10.0)
libvirt:4.5.0
qemu-kvm:2.12.0
2.うまく行かなかった…
初歩的なミスです
下記のサイトを参考にして設定したが、remote-viewer を利用して接続するときに証明書の検証に失敗して接続できなかった。
参考にしたサイト
[ArchWiki]QEMU – 7.2.1.2 TLS 暗号化
発生したエラー
$ remote-viewer --spice-ca-file=./ca-cert.pem spice://testkvm.alprovs.com?tls-port=5900 --spice-secure-channels=all (remote-viewer:17375): Spice-WARNING **: 10:20:02.208: ssl_verify.c:479:openssl_verify: Error in server certificate verification: self signed certificate (num=18:depth0:/C=IL/L=Raanana/O=Red Hat/CN=testkvm.alprovs.com) (remote-viewer:17375): GSpice-WARNING **: 10:20:02.208: main-1:0: SSL_connect: error:00000001:lib(0):func(0):reason(1)
【原因】
認証局の証明書とサーバ証明書の Subject に全く同じものを指定していたから(寝ぼけてたのかね…笑)。
なんで!?と思った方はサーバ証明書の検証の仕組みを調べてください。
# openssl x509 -noout -subject -in ca-cert.pem subject= /C=IL/L=Raanana/O=Red Hat/CN=testkvm.alprovs.com # openssl x509 -noout -subject -in server-cert.pem subject= /C=IL/L=Raanana/O=Red Hat/CN=testkvm.alprovs.com
【修正後】
以下のようにサーバ証明書のCNにはホスト名、認証局の証明書のCNにはサーバ証明書とは異なるものを指定する
# openssl x509 -noout -subject -in ca-cert.pem subject= /C=IL/L=Raanana/O=Red Hat/CN=My CA # openssl x509 -noout -subject -in server-cert.pem subject= /C=IL/L=Raanana/O=Red Hat/CN=testkvm.alprovs.com
そうすると接続できます。
※一度仮想マシンの電源を一度落としてから起動する必要があります。再起動ではダメです。
3.プライベート認証局の構築とサーバ証明書の発行
くだらないことに時間を取ってしまったので、せっかくなら virt-manager もTLS接続できるようにしようと思った。
virt-manager をTLS接続するにはクライアント証明書も必要となって来るので、プライベート認証局を2のような簡易的な方法ではなくもうちょっとしっかりした方法で構築する。プライベート認証局を構築するのに以下のサイトを参考にした。
参考サイト
[Qiita]プライベート認証局(CA)にてクライアント証明書の発行
1.必要なパッケージのインストール
# yum install openssl
2.プライベート認証局の構築
・有効期限が10年になるように /etc/pki/tls/misc/CA と /etc/pki/tls/openssl.cnf を変更する
# cp -p /etc/pki/tls/misc/CA /etc/pki/tls/misc/CA.org # vi /etc/pki/tls/misc/CA ← 編集内容は次の差分を参照 # diff -u /etc/pki/tls/misc/CA.org /etc/pki/tls/misc/CA --- /etc/pki/tls/misc/CA.org 2019-03-10 14:38:59.303623185 +0900 +++ /etc/pki/tls/misc/CA 2019-03-10 14:47:21.189765355 +0900 @@ -60,8 +60,8 @@ if [ -z "$OPENSSL" ]; then OPENSSL=openssl; fi -if [ -z "$DAYS" ] ; then DAYS="-days 365" ; fi # 1 year -CADAYS="-days 1095" # 3 years +if [ -z "$DAYS" ] ; then DAYS="-days 3650" ; fi # 10 year +CADAYS="-days 3650" # 10 years REQ="$OPENSSL req $SSLEAY_CONFIG" CA="$OPENSSL ca $SSLEAY_CONFIG" VERIFY="$OPENSSL verify"■/etc/pki/tls/openssl.cnf 差分
# cp -p /etc/pki/tls/openssl.cnf /etc/pki/tls/openssl.cnf.org # vi /etc/pki/tls/openssl.cnf ← 編集内容は次の差分を参照 # diff -u /etc/pki/tls/openssl.cnf.org /etc/pki/tls/openssl.cnf --- /etc/pki/tls/openssl.cnf.org 2019-03-10 14:54:17.857436143 +0900 +++ /etc/pki/tls/openssl.cnf 2019-03-10 14:59:40.984478950 +0900 @@ -70,7 +70,7 @@ # crlnumber must also be commented out to leave a V1 CRL. # crl_extensions = crl_ext -default_days = 365 # how long to certify for +default_days = 3650 # how long to certify for default_crl_days= 30 # how long before next CRL default_md = sha256 # use SHA-256 by default preserve = no # keep passed DN ordering @@ -127,25 +127,25 @@ [ req_distinguished_name ] countryName = Country Name (2 letter code) -countryName_default = XX +countryName_default = JP countryName_min = 2 countryName_max = 2 stateOrProvinceName = State or Province Name (full name) -#stateOrProvinceName_default = Default Province +stateOrProvinceName_default = Tokyo localityName = Locality Name (eg, city) -localityName_default = Default City +localityName_default = Chiyoda 0.organizationName = Organization Name (eg, company) -0.organizationName_default = Default Company Ltd +0.organizationName_default = hogehoge Company Ltd # we can do this but it is not needed normally :-) #1.organizationName = Second Organization Name (eg, company) #1.organizationName_default = World Wide Web Pty Ltd organizationalUnitName = Organizational Unit Name (eg, section) -#organizationalUnitName_default = +organizationalUnitName_default = hogehoge commonName = Common Name (eg, your name or your server\'s hostname) commonName_max = 64
・認証局の証明書を作成
■認証局用のopenssl設定ファイル# cp -p /etc/pki/tls/openssl.cnf /etc/pki/tls/openssl-ca.cnf # vi /etc/pki/tls/openssl-ca.cnf ← 編集内容は次の差分を参照 # diff -u /etc/pki/tls/openssl.cnf /etc/pki/tls/openssl-ca.cnf --- /etc/pki/tls/openssl.cnf 2019-03-10 14:59:40.984478950 +0900 +++ /etc/pki/tls/openssl-ca.cnf 2019-03-10 15:07:50.990630381 +0900 @@ -169,7 +169,7 @@ # This goes against PKIX guidelines but some CAs do it and some software # requires this to avoid interpreting an end user certificate as a CA. -basicConstraints=CA:FALSE +basicConstraints=CA:TRUE # Here are some examples of the usage of nsCertType. If it is omitted # the certificate can be used for anything *except* object signing. @@ -247,7 +247,7 @@ # keyUsage = cRLSign, keyCertSign # Some might want this also -# nsCertType = sslCA, emailCA +nsCertType = sslCA, emailCA # Include email address in subject alt name: another PKIX recommendation # subjectAltName=email:copy■プライベート認証局のキーと証明書の作成
# cd /etc/pki/tls/
# SSLEAY_CONFIG="-config /etc/pki/tls/openssl-ca.cnf" /etc/pki/tls/misc/CA -newca
CA certificate filename (or enter to create)
← 空Enter
Making CA certificate ...
Generating a 2048 bit RSA private key
..................................................................+++
...+++
writing new private key to '/etc/pki/CA/private/./cakey.pem'
Enter PEM pass phrase: ← パスワード①
Verifying - Enter PEM pass phrase: ← パスワード①
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [JP]: ← 任意
State or Province Name (full name) [Tokyo]: ← 任意
Locality Name (eg, city) [Chiyoda]: ← 任意
Organization Name (eg, company) [hogehoge Company Ltd]: ← 任意
Organizational Unit Name (eg, section) [hogehoge]: ← 任意
Common Name (eg, your name or your server's hostname) []:My Private CA ← 任意の値を入力
Email Address []: ← 任意
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []: ← 空Enter
An optional company name []: ← 空Enter
Using configuration from /etc/pki/tls/openssl-ca.cnf
Enter pass phrase for /etc/pki/CA/private/./cakey.pem: ← パスワード①
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
ed:f0:4b:3a:38:3f:26:6e
Validity
Not Before: Mar 10 06:13:08 2019 GMT
Not After : Mar 7 06:13:08 2029 GMT
Subject:
countryName = JP
stateOrProvinceName = Tokyo
organizationName = hogehoge Company Ltd
organizationalUnitName = hogehoge
commonName = My Private CA
X509v3 extensions:
X509v3 Subject Key Identifier:
AD:E0:9E:BC:CC:79:E3:53:B7:40:A6:06:89:19:41:6D:D7:DE:5C:21
X509v3 Authority Key Identifier:
keyid:AD:E0:9E:BC:CC:79:E3:53:B7:40:A6:06:89:19:41:6D:D7:DE:5C:21
X509v3 Basic Constraints:
CA:TRUE
Certificate is to be certified until Mar 7 06:13:08 2029 GMT (3650 days)
Write out database with 1 new entries
Data Base Updated
■作成されるファイル(認証局構築)
/etc/pki/CA/cacert.pem ← 認証局の証明書 /etc/pki/CA/careq.pem ← 認証局の証明書署名要求(認証局の公開鍵) /etc/pki/CA/index.txt ← 証明書管理情報 /etc/pki/CA/index.txt.attr ← 属性 /etc/pki/CA/index.txt.old ← バックアップ /etc/pki/CA/serial ← シリアル /etc/pki/CA/private/cakey.pem ← 認証局の秘密鍵
3.サーバ証明書の発行
■サーバ証明書用openssl設定ファイル作成# cp -p /etc/pki/tls/openssl.cnf /etc/pki/tls/openssl-server.cnf # vi /etc/pki/tls/openssl-server.cnf # diff -u /etc/pki/tls/openssl.cnf /etc/pki/tls/openssl-server.cnf --- /etc/pki/tls/openssl.cnf 2019-03-10 14:59:40.984478950 +0900 +++ /etc/pki/tls/openssl-server.cnf 2019-03-10 15:31:30.218333055 +0900 @@ -175,7 +175,7 @@ # the certificate can be used for anything *except* object signing. # This is OK for an SSL server. -# nsCertType = server +nsCertType = server # For an object signing certificate this would be used. # nsCertType = objsign■サーバ証明書の証明書署名要求を作成
# cd /etc/pki/tls/ # SSLEAY_CONFIG="-config /etc/pki/tls/openssl-server.cnf" /etc/pki/tls/misc/CA -newreq Generating a 2048 bit RSA private key ......................................+++ ..........................................+++ writing new private key to 'newkey.pem' Enter PEM pass phrase: ← パスワード② Verifying - Enter PEM pass phrase: ← パスワード② ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [JP]: ← 任意 State or Province Name (full name) [Tokyo]: ← 任意 Locality Name (eg, city) [Chiyoda]: ← 任意 Organization Name (eg, company) [hogehoge Company Ltd]: ← 任意 Organizational Unit Name (eg, section) [hogehoge]: ← 任意 Common Name (eg, your name or your server's hostname) []:testkvm.alprovs.com ← 証明したサーバのドメイン or IP Email Address []: ← 任意 Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: ← 空Enter An optional company name []: ← 空Enter Request is in newreq.pem, private key is in newkey.pem■サーバ証明書にプライベート認証局の署名を入れる
# cd /etc/pki/tls/
# SSLEAY_CONFIG="-config /etc/pki/tls/openssl-server.cnf" /etc/pki/tls/misc/CA -sign
Using configuration from /etc/pki/tls/openssl-server.cnf
Enter pass phrase for /etc/pki/CA/private/cakey.pem: ← パスワード②
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
ed:f0:4b:3a:38:3f:26:6f
Validity
Not Before: Mar 10 06:40:55 2019 GMT
Not After : Mar 7 06:40:55 2029 GMT
Subject:
countryName = JP
stateOrProvinceName = Tokyo
localityName = Chiyoda
organizationName = hogehoge Company Ltd
organizationalUnitName = hogehoge
commonName = testkvm.alprovs.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
EC:8C:1A:00:0F:F7:44:B7:65:06:78:9B:E7:32:71:68:81:A8:FA:DC
X509v3 Authority Key Identifier:
keyid:AD:E0:9E:BC:CC:79:E3:53:B7:40:A6:06:89:19:41:6D:D7:DE:5C:21
Certificate is to be certified until Mar 7 06:40:55 2029 GMT (3650 days)
Sign the certificate? [y/n]:y ← yを入力
1 out of 1 certificate requests certified, commit? [y/n]y ← yを入力
Write out database with 1 new entries
Data Base Updated
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
ed:f0:4b:3a:38:3f:26:6f
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=JP, ST=Tokyo, O=hogehoge Company Ltd, OU=hogehoge, CN=My Private CA
Validity
Not Before: Mar 10 06:40:55 2019 GMT
Not After : Mar 7 06:40:55 2029 GMT
Subject: C=JP, ST=Tokyo, L=Chiyoda, O=hogehoge Company Ltd, OU=hogehoge, CN=testkvm.alprovs.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:a9:2d:37:32:66:2f:b0:db:f6:ea:d3:bd:c0:66:
df:02:6a:6c:d7:97:35:ad:59:2f:70:a3:29:58:1f:
f7:36:99:77:0d:df:b5:02:1c:81:cd:e7:f5:d5:c6:
b1:df:10:46:00:a1:8f:e7:03:08:9c:15:f8:5e:bd:
b7:18:d3:65:67:09:e6:83:68:8a:af:53:43:95:f6:
99:1c:16:c4:f8:52:6d:83:ea:55:76:cf:1e:ad:c4:
90:b6:27:96:1d:1e:d4:ee:44:9d:41:07:33:24:eb:
89:03:a3:07:ab:60:64:4e:34:67:67:e2:47:83:f3:
a1:8d:d1:ce:0c:c7:a0:28:f7:e0:41:e9:43:29:92:
b9:19:74:9f:f8:bb:30:bd:a5:b1:dd:65:94:35:91:
9d:aa:e7:2c:11:da:fd:c8:6d:3e:13:ec:8a:c8:e5:
bf:b3:f6:52:63:74:b6:a8:7b:cb:c7:16:f1:c5:1a:
a5:0e:59:69:f9:b6:85:d5:36:cf:1a:d5:65:66:c8:
2a:46:fc:f7:e5:db:c8:d0:da:ce:06:57:c0:ab:67:
c2:94:8c:38:2e:1c:bf:63:b2:eb:9e:ba:3f:46:49:
19:8b:d2:40:d3:72:b1:f1:cd:1d:d1:c2:d1:38:86:
cf:3f:f9:4c:c9:2d:f4:e0:f3:62:30:33:8b:db:d8:
23:d9
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
EC:8C:1A:00:0F:F7:44:B7:65:06:78:9B:E7:32:71:68:81:A8:FA:DC
X509v3 Authority Key Identifier:
keyid:AD:E0:9E:BC:CC:79:E3:53:B7:40:A6:06:89:19:41:6D:D7:DE:5C:21
Signature Algorithm: sha256WithRSAEncryption
94:8f:a4:84:1a:6f:03:8e:d5:6a:c7:6e:17:d9:66:cd:d3:2f:
48:9c:81:c9:bb:a8:23:23:47:50:f2:25:5c:5b:12:b6:47:73:
00:ec:0e:0f:54:07:1b:85:c2:9a:c1:8e:ff:af:13:9f:2b:0d:
b1:f8:19:af:d9:f2:d0:7e:fc:f7:51:9d:c8:f2:9d:f5:1e:3c:
70:ee:6b:7f:bb:6c:07:a3:31:f1:34:36:a9:25:ed:bc:ad:d9:
57:ac:55:05:49:7a:33:5c:8d:4a:e5:7a:6a:f9:5e:8f:03:37:
d0:bc:f3:7b:73:51:c7:44:eb:2c:b8:e4:3d:b4:8b:c4:84:7f:
25:12:b7:41:d0:d6:54:6d:6f:bd:b1:f8:84:6f:3c:7e:b9:31:
10:0b:e0:12:62:87:4e:c4:c3:48:eb:2d:64:5f:48:61:30:ef:
b6:59:56:2c:d6:9f:42:3f:c1:aa:e1:63:99:06:70:db:c9:b3:
9b:54:25:e4:1a:04:59:db:e4:48:72:d1:3b:4b:2d:24:ea:21:
0c:81:34:03:9e:4d:74:6f:4a:3d:2a:97:b1:f1:bd:01:dd:c2:
56:cc:77:c8:1d:d9:4e:8b:0d:96:3d:3d:c5:42:6e:0d:36:5c:
07:a8:90:16:91:a7:83:99:2d:07:68:1b:4c:16:05:9a:00:32:
f3:0b:29:65
-----BEGIN CERTIFICATE-----
MIID5DCCAsygAwIBAgIJAO3wSzo4PyZvMA0GCSqGSIb3DQEBCwUAMGcxCzAJBgNV
BAYTAkpQMQ4wDAYDVQQIDAVUb2t5bzEdMBsGA1UECgwUaG9nZWhvZ2UgQ29tcGFu
eSBMdGQxETAPBgNVBAsMCGhvZ2Vob2dlMRYwFAYDVQQDDA1NeSBQcml2YXRlIENB
MB4XDTE5MDMxMDA2NDA1NVoXDTI5MDMwNzA2NDA1NVowfzELMAkGA1UEBhMCSlAx
DjAMBgNVBAgMBVRva3lvMRAwDgYDVQQHDAdDaGl5b2RhMR0wGwYDVQQKDBRob2dl
aG9nZSBDb21wYW55IEx0ZDERMA8GA1UECwwIaG9nZWhvZ2UxHDAaBgNVBAMME3Rl
c3Rrdm0uYWxwcm92cy5jb20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIB
AQCpLTcyZi+w2/bq073AZt8CamzXlzWtWS9woylYH/c2mXcN37UCHIHN5/XVxrHf
EEYAoY/nAwicFfhevbcY02VnCeaDaIqvU0OV9pkcFsT4Um2D6lV2zx6txJC2J5Yd
HtTuRJ1BBzMk64kDowerYGRONGdn4keD86GN0c4Mx6Ao9+BB6UMpkrkZdJ/4uzC9
pbHdZZQ1kZ2q5ywR2v3IbT4T7IrI5b+z9lJjdLaoe8vHFvHFGqUOWWn5toXVNs8a
1WVmyCpG/Pfl28jQ2s4GV8CrZ8KUjDguHL9jsuueuj9GSRmL0kDTcrHxzR3RwtE4
hs8/+UzJLfTg82IwM4vb2CPZAgMBAAGjezB5MAkGA1UdEwQCMAAwLAYJYIZIAYb4
QgENBB8WHU9wZW5TU0wgR2VuZXJhdGVkIENlcnRpZmljYXRlMB0GA1UdDgQWBBTs
jBoAD/dEt2UGeJvnMnFogaj63DAfBgNVHSMEGDAWgBSt4J68zHnjU7dApgaJGUFt
195cITANBgkqhkiG9w0BAQsFAAOCAQEAlI+khBpvA47VasduF9lmzdMvSJyBybuo
IyNHUPIlXFsStkdzAOwOD1QHG4XCmsGO/68TnysNsfgZr9ny0H7891GdyPKd9R48
cO5rf7tsB6Mx8TQ2qSXtvK3ZV6xVBUl6M1yNSuV6avlejwM30Lzze3NRx0TrLLjk
PbSLxIR/JRK3QdDWVG1vvbH4hG88frkxEAvgEmKHTsTDSOstZF9IYTDvtllWLNaf
Qj/BquFjmQZw28mzm1Ql5BoEWdvkSHLRO0stJOohDIE0A55NdG9KPSqXsfG9Ad3C
Vsx3yB3ZTosNlj09xUJuDTZcB6iQFpGng5ktB2gbTBYFmgAy8wspZQ==
-----END CERTIFICATE-----
Signed certificate is in newcert.pem
■作成されたファイルの確認
/etc/pki/tls/newcert.pem ← サーバ証明書 /etc/pki/tls/newkey.pem ← サーバ秘密鍵 /etc/pki/tls/newreq.pem ← サーバ証明書署名要求(サーバ公開鍵)■作成したファイルの移動
# mv /etc/pki/tls/newcert.pem /etc/pki/CA/certs/testkvm.alprovs.com.crt # mv /etc/pki/tls/newreq.pem /etc/pki/CA/certs/testkvm.alprovs.com.csr # サーバ秘密鍵からパスワードを取り除く # openssl rsa -in /etc/pki/tls/newkey.pem -out /etc/pki/CA/private/testkvm.alprovs.com.key Enter pass phrase for /etc/pki/tls/newkey.pem: ← パスワード② writing RSA key
4.クライアント証明書の発行
■クライアント証明書用 openssl 設定ファイルの作成# cp -p /etc/pki/tls/openssl.cnf /etc/pki/tls/openssl-client.cnf # vi /etc/pki/tls/openssl-client.cnf # diff -u /etc/pki/tls/openssl.cnf /etc/pki/tls/openssl-client.cnf --- /etc/pki/tls/openssl.cnf 2019-03-10 14:59:40.984478950 +0900 +++ /etc/pki/tls/openssl-client.cnf 2019-03-10 15:52:30.265778665 +0900 @@ -184,7 +184,7 @@ # nsCertType = client, email # and for everything including object signing: -# nsCertType = client, email, objsign +nsCertType = client, email, objsign # This is typical in keyUsage for a client certificate. # keyUsage = nonRepudiation, digitalSignature, keyEncipherment■クライアント証明書署名要求を作成
# cd /etc/pki/tls/ # SSLEAY_CONFIG="-config /etc/pki/tls/openssl-client.cnf" /etc/pki/tls/misc/CA -newreq Generating a 2048 bit RSA private key ........................................................................................................+++ ..........................+++ writing new private key to 'newkey.pem' Enter PEM pass phrase: ← パスワード③ Verifying - Enter PEM pass phrase: ← パスワード③ ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [JP]: ← 任意 State or Province Name (full name) [Tokyo]: ← 任意 Locality Name (eg, city) [Chiyoda]: ← 任意 Organization Name (eg, company) [hogehoge Company Ltd]: ← 任意 Organizational Unit Name (eg, section) [hogehoge]: ← 任意 Common Name (eg, your name or your server's hostname) []:hoge user ← 任意のユーザ名を入力 Email Address []: ← 任意 Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: ← 空Enter An optional company name []: ← 空Enter Request is in newreq.pem, private key is in newkey.pem■クライアント証明書を作成
# cd /etc/pki/tls/
# SSLEAY_CONFIG="-config /etc/pki/tls/openssl-client.cnf" /etc/pki/tls/misc/CA -sign
Using configuration from /etc/pki/tls/openssl-client.cnf
Enter pass phrase for /etc/pki/CA/private/cakey.pem: ← パスワード③
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number:
ed:f0:4b:3a:38:3f:26:70
Validity
Not Before: Mar 10 06:58:22 2019 GMT
Not After : Mar 7 06:58:22 2029 GMT
Subject:
countryName = JP
stateOrProvinceName = Tokyo
localityName = Chiyoda
organizationName = hogehoge Company Ltd
organizationalUnitName = hogehoge
commonName = hoge user
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
FF:E5:B7:D5:69:45:26:3A:D3:B7:81:DC:EC:B0:A5:59:E9:98:66:0C
X509v3 Authority Key Identifier:
keyid:AD:E0:9E:BC:CC:79:E3:53:B7:40:A6:06:89:19:41:6D:D7:DE:5C:21
Certificate is to be certified until Mar 7 06:58:22 2029 GMT (3650 days)
Sign the certificate? [y/n]:y ← yを入力
1 out of 1 certificate requests certified, commit? [y/n]y ← yを入力
Write out database with 1 new entries
Data Base Updated
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
ed:f0:4b:3a:38:3f:26:70
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=JP, ST=Tokyo, O=hogehoge Company Ltd, OU=hogehoge, CN=My Private CA
Validity
Not Before: Mar 10 06:58:22 2019 GMT
Not After : Mar 7 06:58:22 2029 GMT
Subject: C=JP, ST=Tokyo, L=Chiyoda, O=hogehoge Company Ltd, OU=hogehoge, CN=hoge user
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:c1:45:64:82:99:6e:75:1c:37:6d:a0:0c:d1:cd:
5f:79:80:56:af:72:1b:a2:96:6c:3e:d7:92:2c:03:
f9:80:41:c1:6d:7c:b3:8e:13:6f:9f:81:9b:8f:19:
80:cc:7f:05:3e:99:2a:c2:ab:cf:a1:3a:53:15:5f:
b8:a5:8a:02:80:1c:54:e3:67:28:4b:e1:43:02:d7:
73:0f:99:1e:bc:87:7c:50:ae:75:d6:e2:5e:64:fe:
09:08:6b:57:19:c9:e1:3c:43:df:82:91:aa:16:c9:
ed:64:39:b2:a1:f4:64:22:3c:8d:a2:9f:71:c9:57:
1e:4a:ba:24:18:11:eb:3a:e2:f8:ca:cd:33:36:df:
1d:a7:30:06:69:3e:fd:1d:e8:75:f3:df:da:95:ac:
ac:5f:68:bb:eb:4a:e4:6d:fd:4a:bb:15:a5:bc:8c:
63:86:1c:56:2d:a7:73:b6:bd:54:ac:1a:53:e0:21:
2d:5a:a4:a9:00:61:3b:a6:2f:cd:91:33:15:0c:2b:
7e:64:1c:ed:52:09:f5:c4:f3:64:cb:ae:f3:a0:29:
19:86:f8:cd:1d:10:e7:69:57:19:a4:6c:01:3c:5a:
de:c5:4d:e1:b0:81:90:91:82:a7:26:9a:88:37:d6:
2d:e4:a3:3a:62:85:fb:c7:3f:94:09:ef:95:78:e0:
e0:4b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
FF:E5:B7:D5:69:45:26:3A:D3:B7:81:DC:EC:B0:A5:59:E9:98:66:0C
X509v3 Authority Key Identifier:
keyid:AD:E0:9E:BC:CC:79:E3:53:B7:40:A6:06:89:19:41:6D:D7:DE:5C:21
Signature Algorithm: sha256WithRSAEncryption
40:b8:6e:a4:21:a1:cd:f4:aa:25:12:49:af:71:e8:28:fe:38:
7d:8e:ab:a6:67:a1:de:c8:e1:62:d7:fe:12:a2:3f:4f:da:32:
2c:50:9f:99:b2:91:40:1d:56:dc:cd:e0:19:27:9d:4f:89:c9:
f2:6b:5d:58:d7:88:47:84:7f:08:da:bc:b0:7c:a9:08:92:db:
11:8f:28:6f:35:a3:21:d0:88:bd:1b:50:1d:f5:f6:4e:59:4d:
62:0c:1d:48:10:f4:d7:4c:46:fd:7b:24:ec:1e:a8:97:1f:70:
cf:87:d2:4e:19:dc:7e:19:e5:d5:59:e5:f5:b8:8b:40:0c:9e:
76:20:de:eb:53:0a:44:bc:7a:ae:e6:83:26:82:eb:0c:81:b3:
1e:12:81:ad:f0:5b:16:ed:9c:0e:49:5d:4f:32:db:aa:a3:a2:
9f:3d:18:a0:ea:bf:d5:a4:57:1f:3c:45:0c:a1:5d:e3:30:ca:
96:bd:90:30:c8:f7:66:2c:30:17:d6:7a:f9:f8:fa:91:a7:bd:
fe:5e:c0:b6:59:37:64:de:cd:a5:36:f3:e1:68:06:6e:3e:22:
52:a7:4e:d5:12:0e:5b:9b:7e:cb:03:9d:ec:0d:3b:72:ad:7c:
66:c8:cb:13:ad:14:10:3e:81:f6:f5:12:3b:0a:9f:63:57:8e:
21:2b:9d:c8
-----BEGIN CERTIFICATE-----
MIID2jCCAsKgAwIBAgIJAO3wSzo4PyZwMA0GCSqGSIb3DQEBCwUAMGcxCzAJBgNV
BAYTAkpQMQ4wDAYDVQQIDAVUb2t5bzEdMBsGA1UECgwUaG9nZWhvZ2UgQ29tcGFu
eSBMdGQxETAPBgNVBAsMCGhvZ2Vob2dlMRYwFAYDVQQDDA1NeSBQcml2YXRlIENB
MB4XDTE5MDMxMDA2NTgyMloXDTI5MDMwNzA2NTgyMlowdTELMAkGA1UEBhMCSlAx
DjAMBgNVBAgMBVRva3lvMRAwDgYDVQQHDAdDaGl5b2RhMR0wGwYDVQQKDBRob2dl
aG9nZSBDb21wYW55IEx0ZDERMA8GA1UECwwIaG9nZWhvZ2UxEjAQBgNVBAMMCWhv
Z2UgdXNlcjCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAMFFZIKZbnUc
N22gDNHNX3mAVq9yG6KWbD7XkiwD+YBBwW18s44Tb5+Bm48ZgMx/BT6ZKsKrz6E6
UxVfuKWKAoAcVONnKEvhQwLXcw+ZHryHfFCuddbiXmT+CQhrVxnJ4TxD34KRqhbJ
7WQ5sqH0ZCI8jaKfcclXHkq6JBgR6zri+MrNMzbfHacwBmk+/R3odfPf2pWsrF9o
u+tK5G39SrsVpbyMY4YcVi2nc7a9VKwaU+AhLVqkqQBhO6YvzZEzFQwrfmQc7VIJ
9cTzZMuu86ApGYb4zR0Q52lXGaRsATxa3sVN4bCBkJGCpyaaiDfWLeSjOmKF+8c/
lAnvlXjg4EsCAwEAAaN7MHkwCQYDVR0TBAIwADAsBglghkgBhvhCAQ0EHxYdT3Bl
blNTTCBHZW5lcmF0ZWQgQ2VydGlmaWNhdGUwHQYDVR0OBBYEFP/lt9VpRSY607eB
3OywpVnpmGYMMB8GA1UdIwQYMBaAFK3gnrzMeeNTt0CmBokZQW3X3lwhMA0GCSqG
SIb3DQEBCwUAA4IBAQBAuG6kIaHN9KolEkmvcego/jh9jqumZ6HeyOFi1/4Soj9P
2jIsUJ+ZspFAHVbczeAZJ51Picnya11Y14hHhH8I2rywfKkIktsRjyhvNaMh0Ii9
G1Ad9fZOWU1iDB1IEPTXTEb9eyTsHqiXH3DPh9JOGdx+GeXVWeX1uItADJ52IN7r
UwpEvHqu5oMmgusMgbMeEoGt8FsW7ZwOSV1PMtuqo6KfPRig6r/VpFcfPEUMoV3j
MMqWvZAwyPdmLDAX1nr5+PqRp73+XsC2WTdk3s2lNvPhaAZuPiJSp07VEg5bm37L
A53sDTtyrXxmyMsTrRQQPoH29RI7Cp9jV44hK53I
-----END CERTIFICATE-----
Signed certificate is in newcert.pem
■作成されたファイルの確認
/etc/pki/tls/newcert.pem ← クライアント証明書 /etc/pki/tls/newkey.pem ← クライアント秘密鍵 /etc/pki/tls/newreq.pem ← クライアント証明書署名要求■クライアント証明書をPKCS#12フォーマットに変換
# cd /etc/pki/tls/ # openssl pkcs12 -export -in newcert.pem -inkey newkey.pem -out hoge_user.pfx -name "hoge_user" Enter pass phrase for newkey.pem: ← パスワード③ Enter Export Password: ← パスワード④ Verifying - Enter Export Password: ← パスワード④■クライアント証明書の移動
# mkdir -p /etc/pki/CA/client/certs/ # mkdir -p /etc/pki/CA/client/private/ # mv /etc/pki/tls/newcert.pem /etc/pki/CA/client/certs/hoge_user.crt # mv /etc/pki/tls/newreq.pem /etc/pki/CA/client/private/hoge_user.csr # mv /etc/pki/tls/newkey.pem /etc/pki/CA/client/private/hoge_user.key # mv /etc/pki/tls/hoge_user.pfx /etc/pki/CA/client/private/
4.SPICEサーバのTLS暗号化設定
■/etc/libvirt/qemu.conf を編集# cp -p /etc/libvirt/qemu.conf /etc/libvirt/qemu.conf.org # vi /etc/libvirt/qemu.conf # diff -u /etc/libvirt/qemu.conf.org /etc/libvirt/qemu.conf --- /etc/libvirt/qemu.conf.org 2019-03-10 16:28:59.161484068 +0900 +++ /etc/libvirt/qemu.conf 2019-03-10 16:29:08.899563006 +0900 @@ -161,7 +161,7 @@ # NB, strong recommendation to enable TLS + x509 certificate # verification when allowing public access # -#spice_listen = "0.0.0.0" +spice_listen = "0.0.0.0" # Enable use of TLS encryption on the SPICE server. @@ -169,7 +169,7 @@ # It is necessary to setup CA and issue a server certificate # before enabling this. # -#spice_tls = 1 +spice_tls = 1 # In order to override the default TLS certificate location for @@ -178,7 +178,7 @@ # If the path is not provided, but spice_tls = 1, then the # default_tls_x509_cert_dir path will be used. # -#spice_tls_x509_cert_dir = "/etc/pki/libvirt-spice" +spice_tls_x509_cert_dir = "/etc/pki/libvirt-spice" # Enable this option to have SPICE served over an automatically created # サービスの再起動 # systemctl restart libvirtd■サーバ証明書・秘密鍵と認証局の証明書を配置
# cp -p /etc/pki/CA/cacert.pem /etc/pki/libvirt-spice/ca-cert.pem # cp -p /etc/pki/CA/certs/testkvm.alprovs.com.crt /etc/pki/libvirt-spice/server-cert.pem # cp -p /etc/pki/CA/private/testkvm.alprovs.com.key /etc/pki/libvirt-spice/server-key.pem
クライアントで認証局の証明書が必要となるのでscpとかでダウンロードする。
■仮想マシンのグラフィックコンソールにTLSで接続$ remote-viewer --spice-ca-file=./cacert.pem spice://testkvm.alprovs.com?tls-port=5900 --spice-secure-channels=all
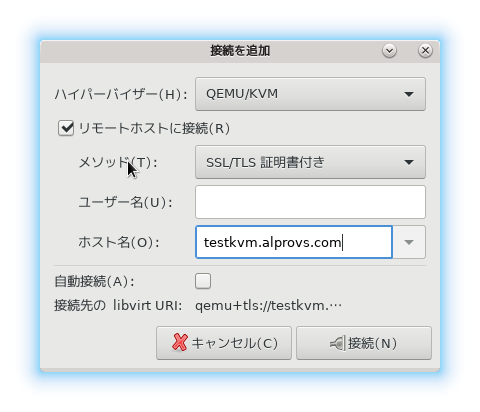
5.virt-managerのTLS接続設定
証明書の配置場所はここに書かれている。
・サーバ側の設定
# cp -p /etc/sysconfig/libvirtd /etc/sysconfig/libvirtd.org # vi /etc/sysconfig/libvirtd # diff -u /etc/sysconfig/libvirtd.org /etc/sysconfig/libvirtd --- /etc/sysconfig/libvirtd.org 2019-01-30 02:33:56.000000000 +0900 +++ /etc/sysconfig/libvirtd 2019-03-10 17:09:27.277619084 +0900 @@ -6,7 +6,7 @@ # Listen for TCP/IP connections # NB. must setup TLS/SSL keys prior to using this -#LIBVIRTD_ARGS="--listen" +LIBVIRTD_ARGS="--listen" # Override Kerberos service keytab for SASL/GSSAPI #KRB5_KTNAME=/etc/libvirt/krb5.tab■/etc/libvirt/libvirtd.conf の編集
# cp -p /etc/libvirt/libvirtd.conf /etc/libvirt/libvirtd.conf.org # vi /etc/libvirt/libvirtd.conf # diff -u /etc/libvirt/libvirtd.conf.org /etc/libvirt/libvirtd.conf --- /etc/libvirt/libvirtd.conf.org 2019-01-30 02:33:56.000000000 +0900 +++ /etc/libvirt/libvirtd.conf 2019-03-10 17:32:58.694964030 +0900 @@ -199,20 +199,20 @@ # Override the default server key file path # -#key_file = "/etc/pki/libvirt/private/serverkey.pem" +key_file = "/etc/pki/CA/private/testkvm.alprovs.com.key" # Override the default server certificate file path # -#cert_file = "/etc/pki/libvirt/servercert.pem" +cert_file = "/etc/pki/CA/certs/testkvm.alprovs.com.crt" # Override the default CA certificate path # -#ca_file = "/etc/pki/CA/cacert.pem" +ca_file = "/etc/pki/CA/cacert.pem" # Specify a certificate revocation list. # # Defaults to not using a CRL, uncomment to enable it -#crl_file = "/etc/pki/CA/crl.pem" +crl_file = "/etc/pki/CA/crl/revoke.crl" ← 証明書の失効情報(利用しない場合はコメントにしておく、利用する場合はおまけを参照) # サービスの再起動とtlsの通信に利用するポートの開放 # systemctl restart libvirtd # firewall-cmd --add-service=libvirt-tls --permanent # firewall-cmd --reload
・クライアント側の設定
クライアント証明書(PKCS#12)をダウンロードしておく。また認証局の証明書もダウンロードしておくこと。
$ openssl pkcs12 -in hoge_user.pfx -out hoge_user.enc.key -nocerts -aes256 Enter Import Password: ← パスワード④ MAC verified OK Enter PEM pass phrase: ← パスワード⑤ Verifying - Enter PEM pass phrase: ← パスワード⑤ $ openssl rsa -in hoge_user.enc.key -out hoge_user.key Enter pass phrase for hoge_user.enc.key: ← パスワード⑤ writing RSA key $ openssl pkcs12 -in hoge_user.pfx -clcerts -nokeys -out hoge_user.crt Enter Import Password: ← パスワード④ MAC verified OK■取り出したクライアント証明書・秘密鍵を配置する
$ mkdir -p ~/.pki/libvirt/ $ mv hoge_user.key ~/.pki/libvirt/clientkey.pem $ mv hoge_user.crt ~/.pki/libvirt/clientcert.pem $ sudo cp cacert.pem /etc/pki/CA/cacert.pem ← 最初 ~/.pki/cacert.pemに配置したがダメだった
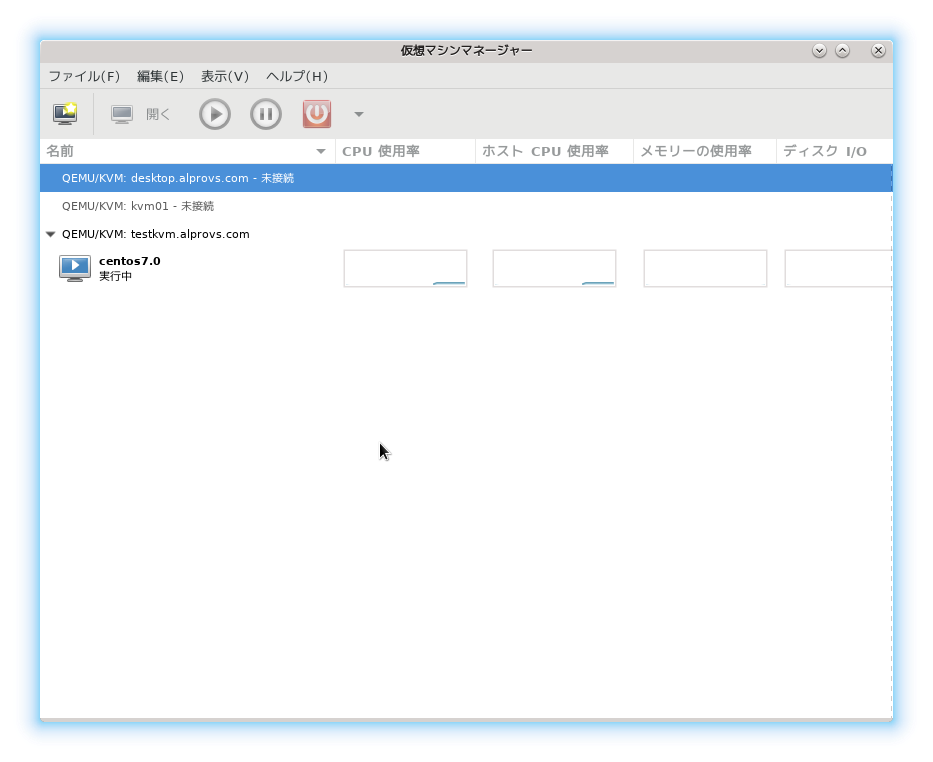
・virt-manager からTLSで接続してみる
クライアント証明書を利用しているためユーザ名は不要
無事接続することが出来た。
以上!
6.おまけ(クライアント証明書を失効させてみる)
/etc/pki/CA/crlnumber が存在しない場合、以下のコマンドを実行する。
■/etc/pki/CA/crlnumber が存在しない場合# echo '00' > /etc/pki/CA/crlnumber■hoge_user を失効
# openssl ca -gencrl -revoke /etc/pki/CA/client/certs/hoge_user.crt -config /etc/pki/tls/openssl-client.cnf Using configuration from /etc/pki/tls/openssl-client.cnf Enter pass phrase for /etc/pki/CA/private/cakey.pem: ← パスワード① -----BEGIN X509 CRL----- MIIB3jCBxwIBATANBgkqhkiG9w0BAQsFADBnMQswCQYDVQQGEwJKUDEOMAwGA1UE CAwFVG9reW8xHTAbBgNVBAoMFGhvZ2Vob2dlIENvbXBhbnkgTHRkMREwDwYDVQQL DAhob2dlaG9nZTEWMBQGA1UEAwwNTXkgUHJpdmF0ZSBDQRcNMTkwMzEwMDkyNzQy WhcNMTkwNDA5MDkyNzQyWjAcMBoCCQDt8Es6OD8mbxcNMTkwMzEwMDc0NjU1WqAO MAwwCgYDVR0UBAMCAQIwDQYJKoZIhvcNAQELBQADggEBACEFVxKF5G63Q+ALfnTg +S2NHOYk7+DiORbasXggAMnN0wvB0SvZuOg3S8LDdFu2f5ZpWNtD3xq8/RXvptZx /ffxLLqFXs6MEsI6BVQC2aHzAlk5WN8L2JmEO+LOahiaeNNvL7aquNf4S1bPilma mUWBxrRntrOa4A/LryRMVCei3Mp+m1jLo5rJs/r3RZaFFQsiKUhg+Jq8xatSMIpZ 8GqUMY5T6pHXNmXW7fM+pAIFH9R8pE8lrx3aih3leomTfSxa4m2On7jwilM6Ar0N IJmGLZEdDbJAKHZkHAnRyuNZ5ZBaKBAeOL/ZNG7fJcjtbEiB/ySfrxwGRl8W8ZB2 9fI= -----END X509 CRL----- Revoking Certificate EDF04B3A383F2670. Data Base Updated■失効証明書リストの更新
# openssl ca -gencrl -out /etc/pki/CA/crl/revoke.crl Using configuration from /etc/pki/tls/openssl.cnf Enter pass phrase for /etc/pki/CA/private/cakey.pem: ← パスワード① # 反映するためにサービスを再起動 # systemctl restart libvirtd
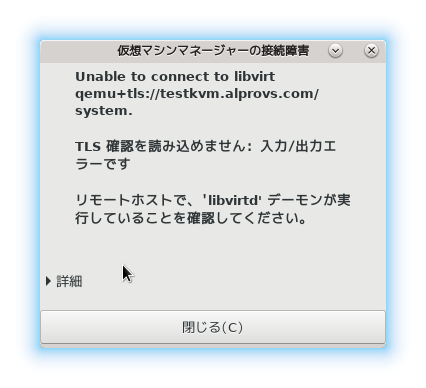
・virt-managerから接続
接続できなくなりました。